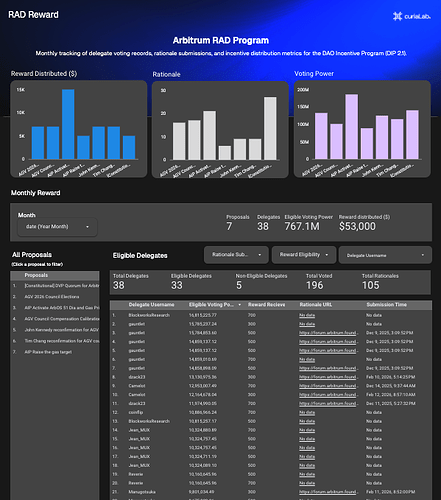
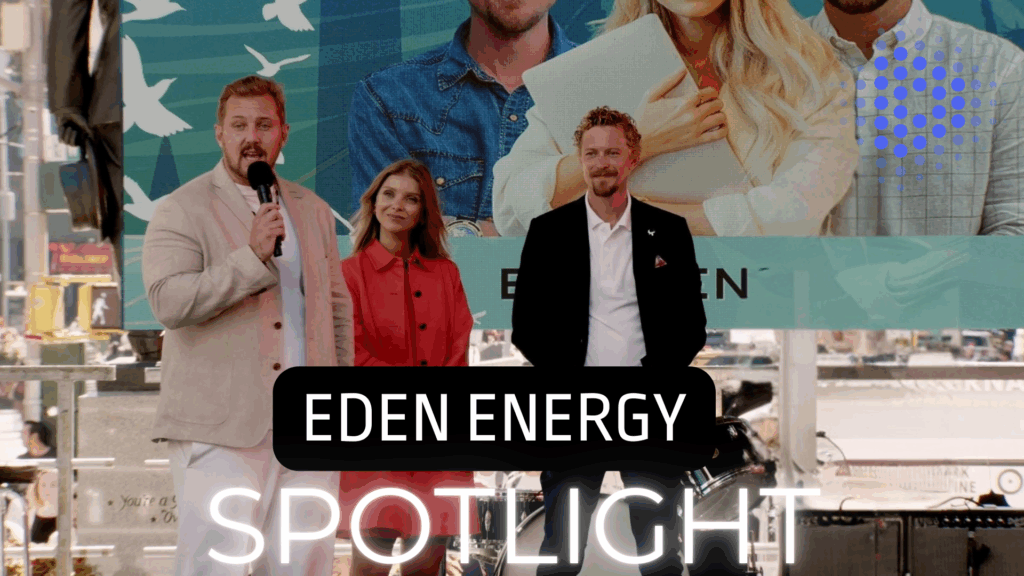
TV Guide - DeFiance Channel
Zoom
00:00
Tuesday 10, 2026
01:00
Tuesday 10, 2026
02:00
Tuesday 10, 2026
03:00
Tuesday 10, 2026
04:00
Tuesday 10, 2026
05:00
Tuesday 10, 2026
06:00
Tuesday 10, 2026
07:00
Tuesday 10, 2026
08:00
Tuesday 10, 2026
09:00
Tuesday 10, 2026
10:00
Tuesday 10, 2026
11:00
Tuesday 10, 2026
12:00
Tuesday 10, 2026
13:00
Tuesday 10, 2026
14:00
Tuesday 10, 2026
15:00
Tuesday 10, 2026
16:00
Tuesday 10, 2026
17:00
Tuesday 10, 2026
18:00
Tuesday 10, 2026
19:00
Tuesday 10, 2026
20:00
Tuesday 10, 2026
21:00
Tuesday 10, 2026
22:00
Tuesday 10, 2026
23:00
Tuesday 10, 2026
00:00
Wednesday 11, 2026
01:00
Wednesday 11, 2026
02:00
Wednesday 11, 2026
03:00
Wednesday 11, 2026
04:00
Wednesday 11, 2026
05:00
Wednesday 11, 2026
06:00
Wednesday 11, 2026
07:00
Wednesday 11, 2026
08:00
Wednesday 11, 2026
09:00
Wednesday 11, 2026
10:00
Wednesday 11, 2026
11:00
Wednesday 11, 2026
12:00
Wednesday 11, 2026
13:00
Wednesday 11, 2026
14:00
Wednesday 11, 2026
15:00
Wednesday 11, 2026
16:00
Wednesday 11, 2026
17:00
Wednesday 11, 2026
18:00
Wednesday 11, 2026
19:00
Wednesday 11, 2026
20:00
Wednesday 11, 2026
21:00
Wednesday 11, 2026
22:00
Wednesday 11, 2026
23:00
Wednesday 11, 2026
00:00
Thursday 12, 2026
01:00
Thursday 12, 2026
02:00
Thursday 12, 2026
03:00
Thursday 12, 2026
04:00
Thursday 12, 2026
05:00
Thursday 12, 2026
06:00
Thursday 12, 2026
07:00
Thursday 12, 2026
08:00
Thursday 12, 2026
09:00
Thursday 12, 2026
10:00
Thursday 12, 2026
11:00
Thursday 12, 2026
12:00
Thursday 12, 2026
13:00
Thursday 12, 2026
14:00
Thursday 12, 2026
15:00
Thursday 12, 2026
16:00
Thursday 12, 2026
17:00
Thursday 12, 2026
18:00
Thursday 12, 2026
19:00
Thursday 12, 2026
20:00
Thursday 12, 2026
21:00
Thursday 12, 2026
22:00
Thursday 12, 2026
23:00
Thursday 12, 2026
News